Warning
Content in this post is for educational purposes only, it may be illegal to carry out the exploit mentioned. The author is not responsible for any action taken against you if you carry it out.
This exploit is possible because of configuration settings in PEAP where certificate validation is not used. As such, even if an invalid certificate is being used, the client will not be notified and will continue to authenticate with the server.
Steps to carry out the exploit:
-
Setup a router with the exact same configuration of the NUS network. WPA2-Enterprise (PEAP-MSCHAPv2).
-
Setup a RADIUS server on a PC and configure it to log down credentials of everyone who connected.
-
Configure the router to use your RADIUS server.
-
Wait for people to connect and steal their NUSNET credentials.
-
Break the NTLM hash to obtain their NUSNET passwords.
I used freeradius-wpe, which does not respond to authentication requests so clients will not be able to complete the connection. The only tell tale sign is a "dead spot" where you cannot connect to NUS network. MSCHAPv2 uses challenge response, so the plaintext password is never sent across the network and hence, we will have to brute force the hash to obtain it.
Since devices will automatically connect to the strongest signal with stored credentials, they just need to walk in range of your router for the connection to happen. If you are adventurous, you might even be able to setup a soft AP with hostapd in place of your router, allowing you to carry out the attack with only a laptop. For long term use, you might want to purchase a router model that NUS uses and mount it nicely somewhere with high human traffic, you could use a raspi as your radius server, connect it to a legit AP and configure it to forward stolen credentials to a server somewhere. It could be months/years before the rogue router is discovered.
I believe the lack of certificate validation might have been for student's convenience. After all, technical support will be very busy if they need to guide students on the process of transferring certificates to their devices and configuring it. It is way simpler to authenticate with only username and password.
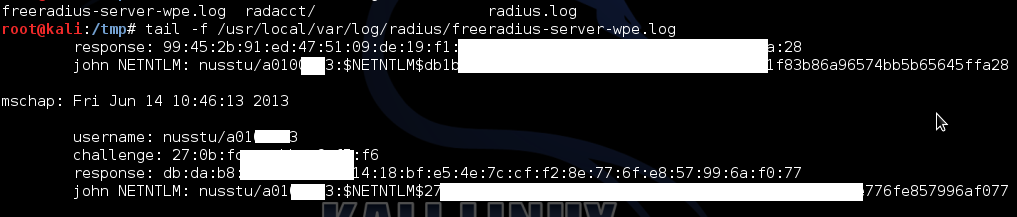
Certain confidential details have been redacted to protect my privacy. The only thing left is to find a GPU cluster to brute force the hash to obtain the passwords. Passwords with 8 or less characters should be "brute forcable" in a reasonable amount of time.