Enumerating sites which are hosted on the same IP address can sometimes tell us a lot about a server. Is it shared hosting? Is it a legitimate server which was compromised for C2 operations? Does the site owner have any other shady business dealings on the side? I am aware that there are sites out there which index the IP address and domain name to provide such a service. However, for this article, I will be touching on manual methods to enumerate these sites.
Subject Alternative Name
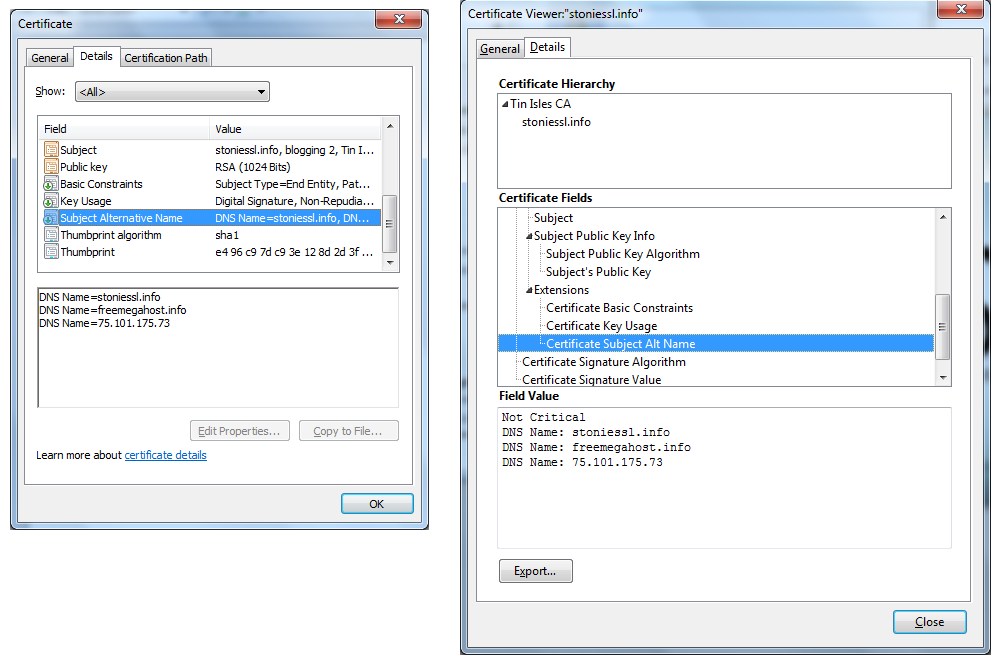
A single SSL cert can be valid for multiple domain names. This method is the easiest as you just need to inspect the cert with a web browser. Such a practice is likely to be done by hobby webmasters. E.g. the boss of a small IT shop might use his company server to host a fan site dedicated to his favourite football team. To prevent such links, webmasters can simply register separate certs for each website they are hosting. This used to be costly since the certs have to be renewed on a regular basis but Lets Encrypt has put that to rest.
Apache Default Vhost
An apache installation will by default serve up the first vhost if a suitable ServerAlias cannot be found. To exploit this, you could nslookup the IP address and attempt to directly visit it in the browser. However, some webmasters might have configured IP-based virtual hosting. To circumvent that, one method I have found to be useful is to register a free DDNS address and point it at that IP and subsequently visit that address in your browser. To prevent such an occurence, webmasters should create a catchall vhost to sinkhole all unknown DDNS addresses pointed to their IP. Take note that the sinkhole vhost has to be the last vhost so it does not sinkhole your actual domain traffic.
No SNI support
An apache installation will also by default serve up the first vhost to a client which does not support SNI. To simulate a such a client, you can run openssl s_client -connect domain.com:443. The previous sinkhole vhost will not work in this case because it has to be the last vhost. In such a case, the webmaster should also register a non-existent domain as the first vhost so as to sinkhole non SNI supported traffic.
Summary
The final vhost configuration should look like this.
1 2 3 4 5 6 7 8 9 10 11 | |
With such a configuration, visitors who visit supersecretsite.com will not be able to find my personal domain and thus not know who is behind the website. Similarly, visitors to my personal domain will not know the existence of supersecretsite.com. All No SNI visitors will be sinkholed by aacatch-nosni-443 while all other random DDNS visitors will be sinkholed by zzcatchall-443. To reiterate, I cannot put zzcatchall-443 right at the top because it will also sinkhole limbenjamin.com and supersecretsite.com. Apache loads config files by alphabetical order, hence I prepended zz to the config to ensure it is the last to be loaded.