Index
Forensics - Walking down a colourful memory lane
OSINT - Sounds of freedom!
Cloud - Find the leaking bucket!
Bonus - Bonus flag for submitting Awesome Write-up
Walking down a colourful memory lane
We are trying to find out how did our machine get infected. What did the user do?
Please view this Document for download instructions.
forensics-challenge-1.mem - 2.0GB
I was kind of dreading this challenge when I first read it. I wouldn't have taken on this case as an ex-cyber forensics analyst. Forensic cases usually have a trigger point where analysis can start, a suspicious executable running on a workstation, a large data upload at a certain time... Finding anything malicious is not forensics, it is a treasure hunt. Are you referring to the adware running on the machine, or do I have to dig much much deeper to get to the UEFI rootkit.
Anyway, to start analysing the memory image, we normally run the volatility imageinfo plugin to determine the OS version. If multiple profiles are returned, the general rule of thumb is to select the most specific profile, the one with release version. It is likely to be a better fit and plugins will have a higher chance of working correctly.
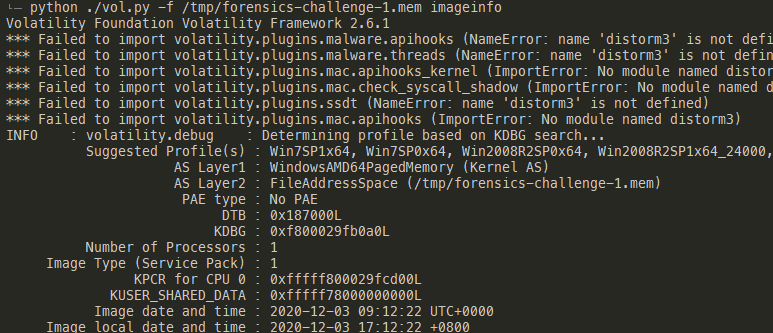
After unsucessfully looking through various forensic artefacts (i.e. event logs, registry...), I decided to look at IE history using the volatility tool. We can see that the user is using IE to download Chrome. We finally have a lead to follow.
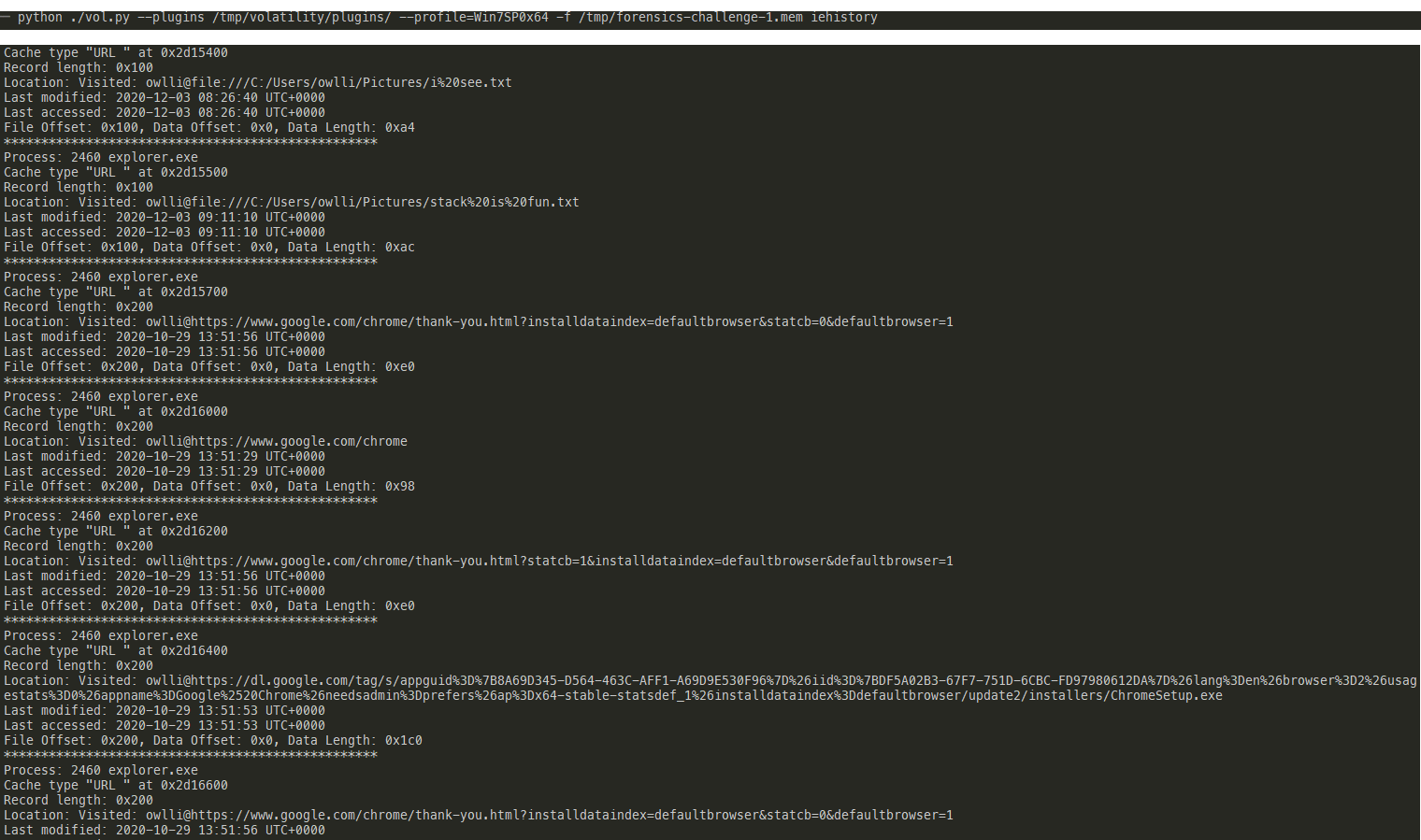
Unfortunately, the chromehistory plugin did not work for me. This is quite common as memory structures and locations may change with every chrome version update. I decided to manually dump the memory of the chrome process and parse the strings from there. The first step is to use the pstree plugin to get the pid of the process and then use the vaddump plugin to dump the memory. We cannot use procdump as it will only dump the process's executable image. The URLs and web page contents are likely in the heap memory. One benefit of using this generic memory dump method is that such methods work across different applications. It will work even if the user uses opera or other obscure browser or application without dedicated plugins.
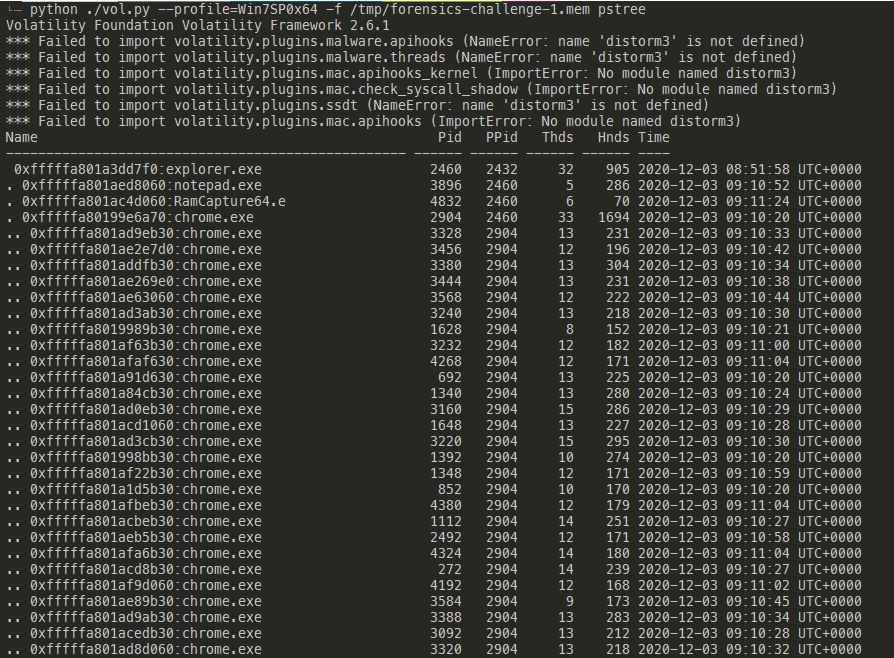
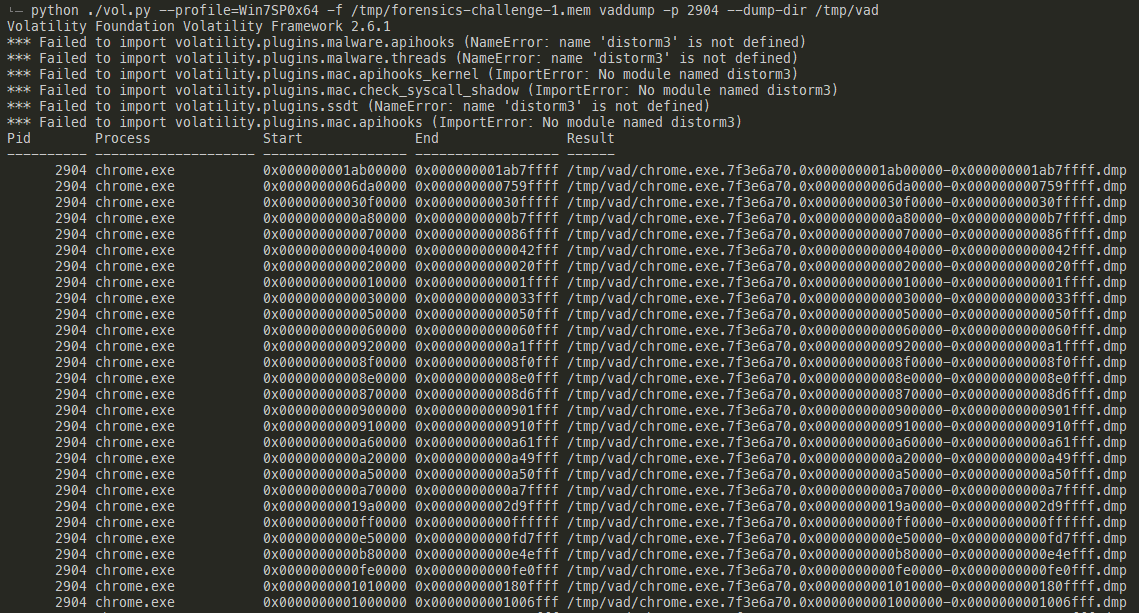
Once the memory has been dumped, I used strings to parse both ASCII and unicode strings from the memory and piped it to a file. Searching for http revealed a mediafire URL that didn't really belong, as the rest of the URLs were related to cybersecurity or govtech.
Upon downloading the png file, I found that it was a tiny 1 row high PNG file and a color picker eventually revealed that the flag was encoded in the individual RGB values of the image. The flag was indeed hidden in a colourful lane!
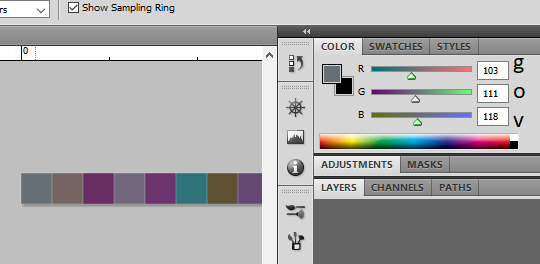
Flag: govtech-csg{m3m0ry_R3dGr33nBlu3z}
Sounds of freedom!
In a recent raid on a suspected COViD hideout, we found this video in a thumbdrive on-site. We are not sure what this video signifies but we suspect COViD's henchmen might be surveying a potential target site for a biological bomb. We believe that the attack may happen soon. We need your help to identify the water body in this video! This will be a starting point for us to do an area sweep of the vicinity!
To me, this was a rather interesting challenge. It is one of the few which does not require any infosecurity knowledge and is fully solvable through observation and logical deduction.
The first clue came from the small road and bus stop opposite. The bus stop is clearly a design seen in Singapore and thus we can conclude that the video is shot in Singapore.
The second clue involved listening to the sounds of freedom, the fighter jets roaring overhead. This suggests that the location is somewhere near the edge of Singapore's airspace, or near one of the airbases.
The third clue came in the form of the aircon compressors. This suggests a residential building since commercial buildings normally have centralised air-conditioning. The more "atas" facade also suggests either a condominium or a more premium form of public housing (i.e. HUDC/DBSS).
Combined with the fact that this building is directly opposite a park with a pond inside of it, a scroll around on google maps reveal a few locations in Singapore that could fulfil these criteria.
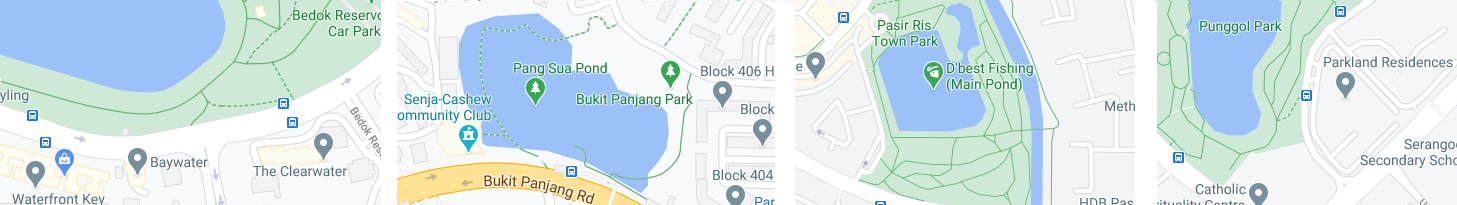
Bedok Reservoir Park - Quickly eliminated because Bedok Reservoir Road is much wider than the road in the video
Bukit Panjang Park - Eliminated because there are no Condos nearby
Pasir Ris Town Park - Eliminated because there are no bus stops along the road next to the park
Punggol Park - Likely candidate
Using Google street view on the 2 bus stops next to the DBSS at Punggol park quickly revealed that one of the bus stops is indeed the location as seen in the video. The video was shot from Parkland Residences Block 475B S(531475) and the postal code of Punggol park is S(538768). Kids, please be mindful before posting your 10 second tiktok videos.
Flag: govtech-csg{538768}

Find the leaking bucket!
It was made known to us that agents of COViD are exfiltrating data to a hidden S3 bucket in AWS! We do not know the bucket name! One tip from our experienced officers is that bucket naming often uses common words related to the company’s business.
Do what you can! Find that hidden S3 bucket (in the format “word1-word2-s4fet3ch”) and find out what was exfiltrated!
This seemed like a rather simple challenge, at least from the get go. cewl is a good tool if you would like to automatically crawl websites for keywords. However, since there are only a few words and some of the words are in image form, I decided to do it manually. I wrote a python script to enumerate all possible word combinations from both the word cloud and the image.
1 2 3 4 5 6 | |
I then used bucket finder to brute force and find the correct S3 bucket.
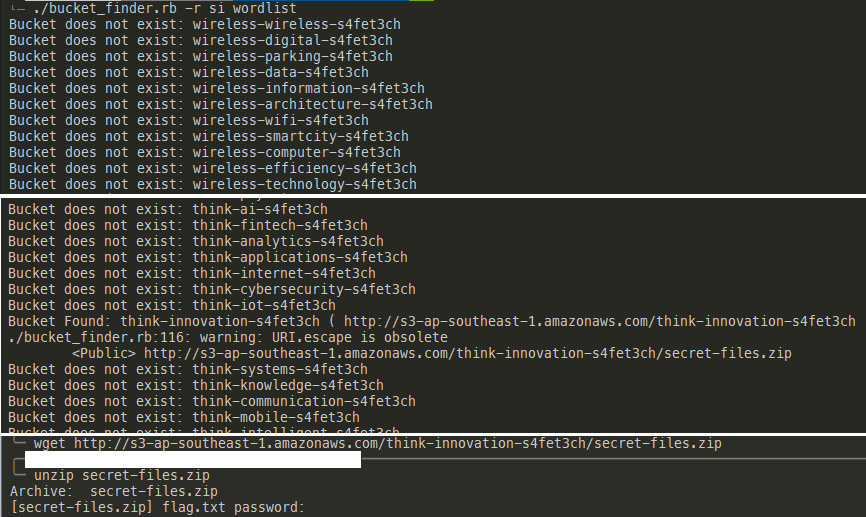
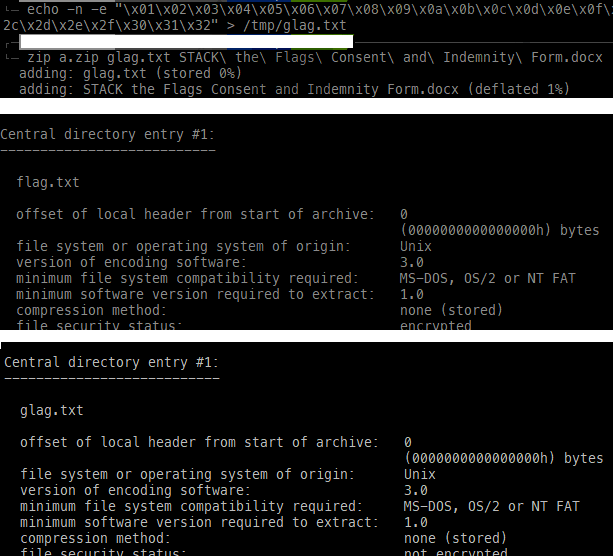
Oh shit, why is it encrypted? Interestingly, there seems to be a second encrypted file in there. Well, if we can find an unencrypted version somewhere on the web, maybe we can launch a known plaintext attack?
I then used pkcrack to perform the known plaintext attack. pkcrack requires us to zip the unencrypted copy using the same zip algorithm as the original encrypted zip file. I have also added a filler flag file named glag.txt just in case it is required.
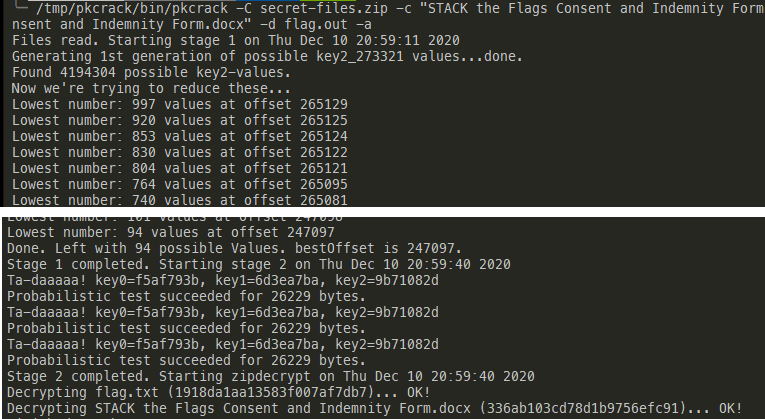
Got it!
Flag: govtech-csg{EnCrYpT!0n_D0e$_NoT_M3@n_Y0u_aR3_s4f3}
Bonus flag for submitting Awesome Write-up
Looks like there are more flags?
Flag: govtech-csg{N5hawwrovddMKXD1xArQ}