Technical prowess, Legal expertise and Guts. That is what you need to go up against a Nation State Adversary. We shall take the Apple vs US Government debate as an example. Apple obviously has the technical prowess to store the iPhone's PIN code securely. If it were easily retrievable, the government would not have had to resort to a legal avenue. Apple also possesses the legal expertise to appeal against the court order and subsequently mount a legal defence. Lastly, it takes some guts to go against the US government.
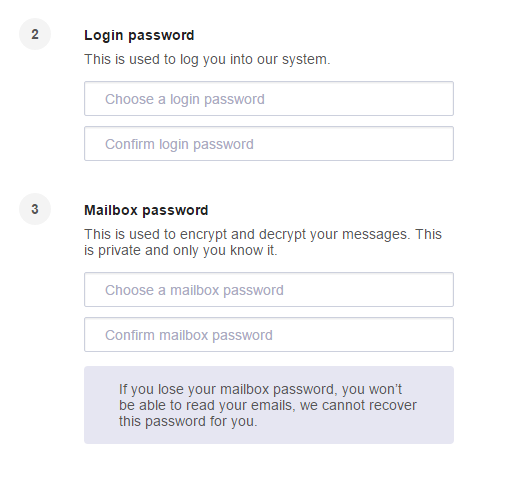
ProtonMail is a secure email service based in Switzerland that promises end-to-end encryption. It takes a fair amount of technical prowess to ensure that the architecture design is sound. ProtonMail uses a novel approach where your private key is symmetrically encrypted with your mailbox password and then uploaded to ProtonMail's server. The mailbox password never leaves the machine and users are authenticated via a different login password. I can see 2 potential flaws with this approach. Firstly, it is probably one of the largest collections of private keys, I bet you that the top 10 most common passwords will successfully decrypt at least 1% of the keys. Secondly, when asked to create 2 passwords, users will likely choose the same password. In the event of a security breach, if the attackers manage to obtain a pre-image of the login password hash, they will be able to decrypt the private key since both passwords are the same. The registration page does not even remind them to use 2 different passwords.
Implementation is yet another nightmare, apart from following the design to spec, developing a secure web application is difficult due to the many layers of abstraction. The web app runs on a browser which runs on the operating system which runs on hardware. The web application is unable to directly access the system memory, hence there is a possibility of portions of the unencrypted private key being left in memory due to improper garbage collection. If there is a vulnerability in the browser, a site in a different tab might be able to escape the sandbox and access the private memory of the web app. Further compounding the problem is the fact that are a whole lot of browsers out there, each with a whole lot of different versions.
A number of events have led me to doubt their technical ability. First, the week long DDOS attack. Yes, it was a sophisticated attack, but the fact remains that they failed to handle it. It was finally resolved after a number of external companies and engineers chipped in to help out. A quick look at their staff profiles reveal that many of them, including a self proclaimed crypto expert, have PhDs in Physics from Ivy League universities. Yes, these are the brightest minds, and yes, it is rocket science. But I wouldn't trust them to do heart bypass surgery, nor do I trust them to design and implement secure computer systems.
Next, the part on legal expertise. ProtonMail seems to bank hard on Swiss privacy laws to save them from the US government. They seem to forget that barely 7 years ago, the US government used FATCA to step all over Swiss banking secrecy laws. Although UBS is a bank based in Switzerland, they had to pay USD780 million in fines and were forced to reveal the names of some of their clients. It is not hard to imagine a future worldwide "anti terrorism bill" forcing ProtonMail to decrypt communications belonging to "suspect terrorists". I doubt ProtonMail even has the funds to hire a lawyer. The payout for their bug bounty program ranges from $50 to $250. I have lived in Geneva, so trust me, USD50 doesn't go far, it is enough for lunch and dinner at the coop supermarket chain and probably a coffee.
Lastly on guts. When ProtonMail was DDOSed, they were pressured by other companies who were also affected into paying the $6000 ransom that was demanded. They caved. I can't imagine them standing against the US government.