Most of the solutions for FLARE-On 5 web2point0 challenge involve the use of a framework to decompile WebAssembly. Chrome offers the ability to debug WebAssembly code which gives us the opportunity to solve this challenge without any other tools.
When solving simpler crackme binaries, we usually look for the strcmp function call near the end of the execution and put a breakpoint there. The reason is that the code which decodes or decrypts the actual password has to run first before the plaintext password is stored in memory and compared to the user input.
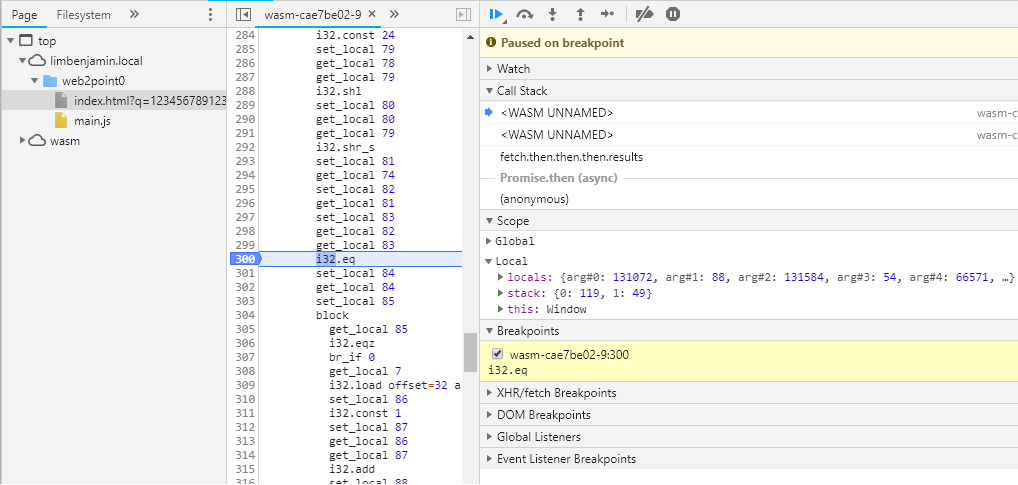
A similar strategy can be used here. We will need to set a breakpoint on Function 9 Line 300, at the i32.eq function call. That operation compares the individual characters of the actual password, the first variable on the stack, with the corresponding character from the user input, the second variable on the stack. The image below shows the first comparison loop. The first character of the password is 119. If we step through, we will get the second character and so on. The full password obtained is 119 97 115 109 95 114 117 108 101 122 95 106 115 95 100 114 111 111 108 122 64 102 108 97 114 101 45 111 110 46 99 111 109, when converted to ascii wasm_rulez_js_droolz@flare-on.com.